Trust Us To Lead The Way In Certification And Compliance
Knowledge And Expertise
Thorough Understanding Of The Framework, Its Requirements, And Best Practices For Implementation
Proven Track Record
Successful Track Record Of Helping Clients Achieve Compliance, With Positive Client Testimonials And Case Studies.
Strong Project Management Skills
Ensure The Compliance Engagement Runs Smoothly And Is Completed On Time And Within Budget.
Experienced Team
Possession Of Experienced Professionals, Including Auditors, Consultants, And Technical Experts
Exceptional Customer Service
Committed To Excellent Customer Service With Clear Communication, Responsive Support, And A Focus On Satisfaction.
Competitive Pricing
We Prioritize Delivering High-Quality Services With Competitive Pricing That Provides Exceptional Value To Our Clients
FAQs
FREQUENTLY ASKED QUESTIONS
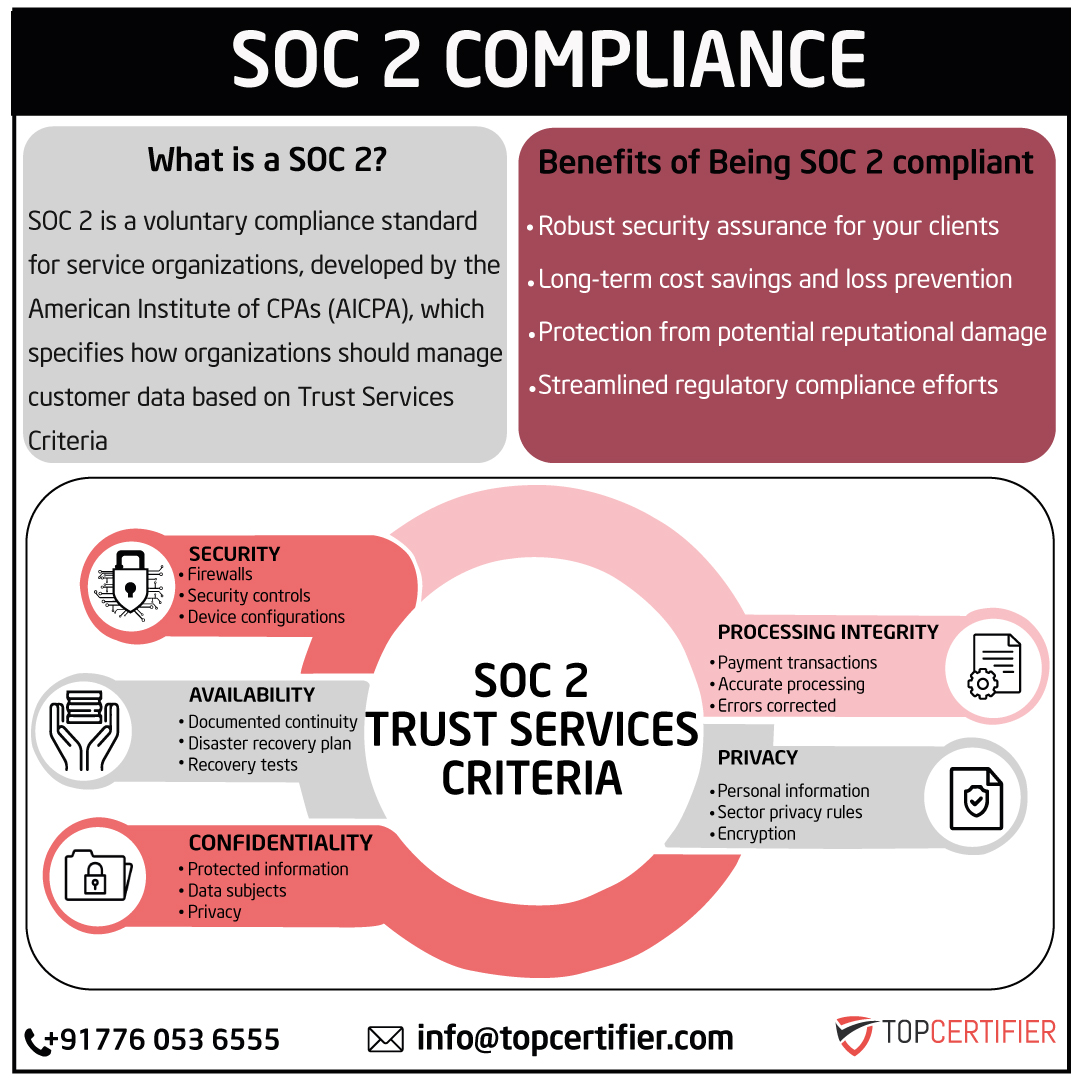
SOC 2 Certification in China is a type of auditing procedure that assesses and reports on the controls used by service organizations to protect the confidentiality, integrity, and availability of their customers' data. It is a widely recognized standard for evaluating and reporting on the effectiveness of a company's information security controls.
In China, SOC 2 certification is governed by the American Institute of Certified Public Accountants (AICPA) and is commonly used by service organizations, such as cloud computing providers, to demonstrate their commitment to security and data protection to their customers. The SOC 2 audit examines the organization's systems, policies, and procedures related to security, availability, processing integrity, confidentiality, and privacy.
Any organization that processes, stores, or transmits sensitive information on behalf of their clients, such as SaaS companies, cloud service providers, and data centers, may need SOC 2 compliance.
There are two types of SOC 2 reports, each serving a distinct purpose in the assessment of an organization's controls.
The SOC 2 Type 1 report focuses on the design of an organization's controls at a specific point in time. Its primary purpose is to evaluate whether the systems and controls are suitably designed to meet the relevant Trust Service Criteria. In this report, the auditor examines the organization's system and the suitability of the design of its controls. This type of report is often used by organizations as an initial step in SOC 2 compliance, providing assurance about the design of controls as of a certain date.
On the other hand, the SOC 2 Type 2 report goes a step further by assessing the operational effectiveness of those controls over a period of time, typically covering a minimum of six months. This report not only reviews the design of the controls but also tests their operational effectiveness throughout the review period. The SOC 2 Type 2 report is more comprehensive and provides users with a higher level of assurance about the organization's control environment. It demonstrates how the controls are managed and maintained over time, offering a more in-depth view of the organization's commitment to maintaining a robust control environment.
SOC 1 compliance focuses on financial reporting controls, while SOC 2 compliance is concerned with controls related to the security, availability, processing integrity, confidentiality, and privacy of data.
To achieve SOC 2 compliance, an organization must first identify the relevant trust services criteria and implement appropriate controls to address them. An independent auditor must then perform an audit to verify that these controls are effective
SOC 2 compliance is not a one-time event, but rather an ongoing process. Organizations must regularly assess and update their controls to maintain compliance and typically undergo an audit on an annual basis.
SOC 2 compliance can provide several benefits, including increased customer trust, improved security and privacy practices, and a competitive advantage in the marketplace.
The cost of SOC 2 compliance varies depending on factors such as the size and complexity of the organization and the scope of the audit. However, the benefits of compliance often outweigh the costs in terms of improved security and increased customer confidence.
SOC 2 (System and Organization Controls 2) and ISO 27001 (International Organization for Standardization 27001) are both information security frameworks used to protect confidential information and mitigate risks. The main difference between SOC 2 Certification in China and ISO 27001 Certification in China is the scope of the framework. SOC 2 is a set of standards created by the American Institute of Certified Public Accountants (AICPA) that focuses on the security, availability, processing integrity, confidentiality, and privacy of data processed by a service organization. SOC 2 is often used by service providers such as data centers, SaaS companies, and cloud computing providers to demonstrate their security controls to customers and auditors. On the other hand, ISO 27001 is a globally recognized standard that specifies the requirements for an information security management system (ISMS). ISO 27001 is applicable to any type of organization, including service providers, and covers a wider range of security controls beyond just the protection of data. The standard also includes requirements for risk assessment, risk management, and continuous improvement. In summary, SOC 2 is a specific set of standards focused on the security of data processed by service organizations, while ISO 27001 is a broader information security framework applicable to any type of organization.